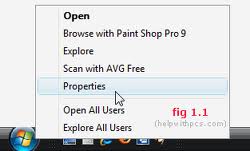
Windows has a nice new Start menu,
which you can customize more thoroughly than you could with the Start
menu in any earlier version of Windows. Open the Taskbar And Start Menu
Properties dialog box by right-clicking the taskbar and clicking
Properties. On the Start Menu tab, select either the Start Menu option
or the Classic Start Menu option to choose which version of the Start
menu to use, and then click Customize. The Customize Start Menu dialog
box appears; you use this box to customize how Windows displays the
Start menu.
The following sections describe
the most useful Start menu hacks. First you learn how to configure what
does and does not appear on the Start menu. Then you learn how to
prevent some programs from appearing on the frequently used programs
list. You also learn how to restore the Start menu’s sort order when
it’s not in alphabetical order.
Configuring the Start Menu’s Contents
Even
though you can completely customize the Start menu in the user
interface, power users and IT professionals will likely want to script
Start menu customizations. Power users don’t want to reconfigure the
Start menu every time they install Windows. IT professionals can use
scripts to deploy these settings or configure them automatically when
creating default user profiles.
If you want to script these
settings, you need to know where to find them in the registry. All
these settings are in the same place:
HKCU\Software\Microsoft\Windows\ CurrentVersion\Explorer\Advanced
The
first section, “Classic Start Menu,” contains values that affect the
classic Start menu. The second section, “New Start Menu,” contains
values that affect the new Start menu, also known as the Start panel.
Most of these settings are REG_DWORD values, but some are REG_SZ
values. If the possible data for any of the settings includes 0×01,
0×02, and so on, that setting is a REG_DWORD value. If the possible
data includes NO or YES, it’s a REG_SZ value.
CLASSIC START MENU
StartMenuAdminTools
0×00–Hide Administrative Tools
0×01–Display Administrative Tools
CascadeControlPanel
NO–Display Control Panel as link
YES–Display Control Panel as menu
CascadeMyDocuments
NO–Display My Documents as link
YES–Display My Documents as menu
CascadeMyPictures
NO–Display My Pictures as link
YES–Display My Pictures as menu
CascadePrinters
NO–Display Printers as link
YES–Display Printers as menu
IntelliMenus
0×00–Don’t use personalized menus
0×01–Use Personalized Menus
CascadeNetworkConnections
NO–Display Network Connections as link
YES–Display Network Connections as menu
Start_LargeMFUIcons
0×00–Show small icons in Start menu
0×01–Show large icons in Start menu
StartMenuChange
0×00–Disable dragging and dropping
0×01–Enable dragging and dropping
StartMenuFavorites
0×00–Hide Favorites
0×01–Display Favorites
StartMenuLogoff
0×00–Hide Log Off
0×01–Display Log Off
StartMenuRun
0×00–Hide Run command
0×01–Display Run command
StartMenuScrollPrograms
NO–Don’t scroll Programs menu
YES–Scroll Programs menu
NEW START MENU
Start_ShowControlPanel
0×00–Hide Control Panel
0×01–Show Control Panel as link
0×02–Show Control Panel as menu
Start_EnableDragDrop
0×00–Disable dragging and dropping
0×01–Enable dragging and dropping
StartMenuFavorites
0×00–Hide Favorites menu
0×01–Show Favorites menu
Start_ShowMyComputer
0×00–Hide My Computer
0×01–Show My Computer as link
0×02–Show My Computer as menu
Start_ShowMyDocs
0×00–Hide My Documents
0×01–Show My Documents as link
0×02–Show My Documents as menu
Start_ShowMyMusic
0×00–Hide My Music
0×01–Show My Music as link
0×02–Show My Music as menu
Start_ShowMyPics
0×00–Hide My Pictures
0×01–Show My Pictures as link
0×02–Show My Pictures as menu
Start_ShowNetConn
0×00–Hide Network Connections
0×01–Show Network Connections as link
0×02–Show Network Connections as menu
Start_AdminToolsTemp
0×00–Hide Administrative Tools
0×01–Show on All Programs menu
0×02–Show on All Programs menu and Start menu
Start_ShowHelp
0×00–Hide Help and Support
0×01–Show Help and Support
Start_ShowNetPlaces
0×00–Hide My Network Places
0×01–Show My Network Places
Start_ShowOEMLink
0×00–Hide Manufacturer Link
0×01–Show Manufacturer Link
Start_ShowPrinters
0×00–Hide Printers and Faxes
0×01–Show Printers and Faxes
Start_ShowRun
0×00–Hide Run command
0×01–Show Run command
Start_ShowSearch
0×00–Hide Search command
0×01–Show Search command
Start_ScrollPrograms
0×00–Don’t scroll Programs menu
0×01–Scroll Programs menu